Have you ever wondered how your email reaches its recipient instantly, or how you can seamlessly stream a movie from across the globe? The unsung hero behind these everyday digital marvels is TCP/IP, the Transmission Control Protocol/Internet Protocol suite. More than just an acronym, TCP/IP is the foundational language of the internet, a set of rules and procedures that allows billions of devices worldwide to communicate and exchange data.
Whether you're a curious beginner taking your first steps into networking or an aspiring professional looking to deepen your understanding, this blog post will take you on a journey through the intricate world of TCP/IP, from its fundamental concepts to its advanced mechanisms, including a detailed look at TCP's remarkable reliability features.
The Genesis: Why TCP/IP?
Before TCP/IP became the universal standard, networking was a fragmented landscape. Different manufacturers had their own proprietary communication systems, leading to isolated networks and limited interoperability. The need for a common language was paramount, especially with the emergence of ARPANET (the precursor to the internet) in the 1970s. The U.S. Department of Defense spearheaded the development of TCP/IP to create a robust, reliable, and open standard for communication across diverse networks. This "common rulebook" revolutionized networking, paving the way for the interconnected world we know today.
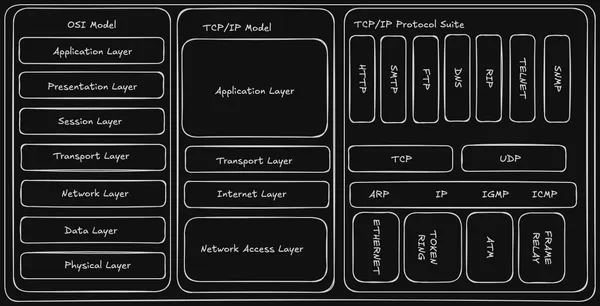
The Foundation: Understanding the TCP/IP Model (The Four Layers)
The TCP/IP model organizes the complex tasks of network communication into a structured, layered approach. Each layer has specific responsibilities, working in harmony to ensure data reaches its destination efficiently and reliably. While sometimes compared to the seven-layer OSI model, the TCP/IP model is typically described with four layers:
1. Application Layer: The User's Interface
This is the topmost layer, closest to the end-user applications. It provides the protocols that allow applications to interact with the network. Think of it as the language your browser uses to talk to a web server, or your email client uses to send and receive messages.
- Key Protocols: HTTP/HTTPS, FTP, SMTP, POP3/IMAP, DNS.
2. Transport Layer: End-to-End Delivery
This layer is responsible for the end-to-end communication between applications on different hosts. It ensures that data segments are delivered reliably and in the correct order, or in some cases, prioritizes speed over guaranteed delivery. This is where the magic of TCP truly shines.
- Key Protocols:
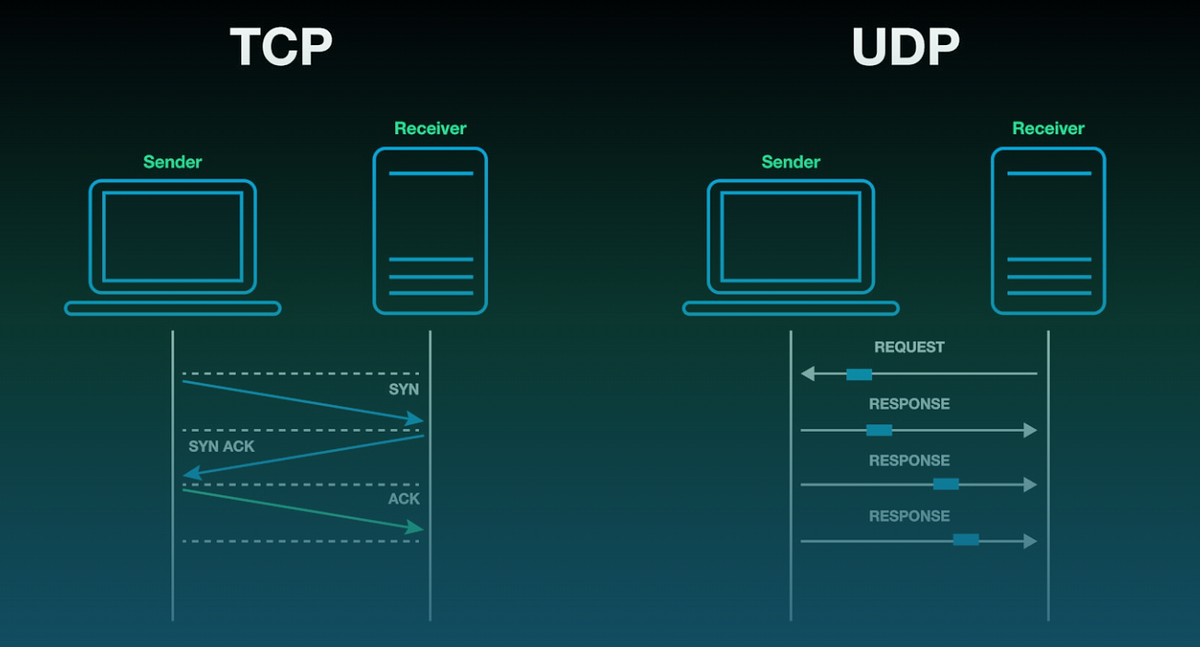
- TCP (Transmission Control Protocol): The "reliable" workhorse. TCP establishes a connection, segments data into smaller pieces (segments), numbers them, and ensures they arrive at the destination in the correct order and without errors. It handles retransmissions of lost packets and manages flow control to prevent overwhelming the receiver. Used for web Browse, email, file transfers, etc.
- UDP (User Datagram Protocol): The "fast and furious" option. UDP is a connectionless protocol that sends data packets (datagrams) without establishing a prior connection or guaranteeing delivery. It's faster and has less overhead, making it suitable for applications where speed is critical and some data loss is acceptable, like online gaming, video streaming, and DNS lookups.
3. Internet Layer (or Network Layer): The Routing Maestro
The Internet layer is the backbone of inter-network communication. Its primary role is to address and route data packets across different networks to their final destination. This is where the "IP" in TCP/IP comes into play.
- Key Protocols: IP, ICMP, ARP.
4. Network Access Layer (or Link Layer): The Physical Connection
This is the lowest layer, dealing with the physical transmission of data over a specific network medium. It defines how data is formatted for transmission over the network and how it interacts with the physical hardware (like network interface cards).
- Key Protocols/Technologies: Ethernet, Wi-Fi (802.11), Device drivers.
How Data Flows: A Packet's Journey
Let's visualize how your data travels using the TCP/IP model:
- Application Layer: You type a URL in your browser (e.g., www.example.com). The browser uses HTTP to request the web page.
- Transport Layer: TCP takes the HTTP request, breaks it into smaller segments, adds a TCP header (including source and destination port numbers, sequence numbers, acknowledgment numbers, and TCP Flags), and hands them to the Internet layer.
- Internet Layer: IP takes each TCP segment, adds an IP header (including source and destination IP addresses), forming an IP packet. It then determines the best route to the destination server.
- Network Access Layer: The IP packet is then encapsulated into a frame, adding a frame header and trailer (including MAC addresses for local network delivery). This frame is then converted into electrical signals, light pulses, or radio waves and sent over the physical medium (e.g., Ethernet cable, Wi-Fi).
This process reverses at the destination, with each layer stripping off its respective header until the original HTTP request is delivered to the web server's application. The server then sends the requested web page back using the same layered process.
Diving Deeper: Advanced TCP/IP Concepts
Now, let's explore the powerful mechanisms that make TCP the reliable workhorse it is.
IP Addressing: IPv4 vs. IPv6
- IPv4 (Internet Protocol version 4): Uses 32-bit addresses (e.g., 192.168.1.1). Depleting address space.
- IPv6 (Internet Protocol version 6): Uses 128-bit addresses, providing a vastly larger address space for future growth.
Subnetting and CIDR
- Subnetting: Dividing a large IP network into smaller, more manageable subnetworks.
- CIDR (Classless Inter-Domain Routing): More efficient IP address allocation and routing, enabling flexible subnetting.
The Heart of Reliability: TCP's Intricate Mechanisms
TCP's magic lies in its ability to provide reliable, ordered, and error-checked delivery of data, even over unreliable networks. This is achieved through a sophisticated set of mechanisms:
1. TCP Segments and Headers
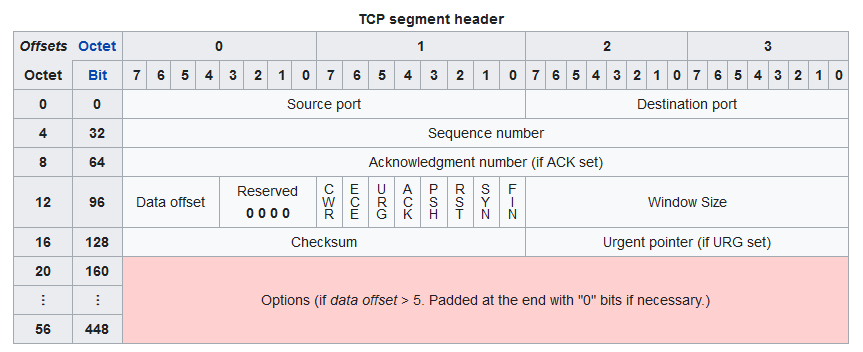
When an application sends data, TCP divides it into smaller units called segments. Each segment includes a TCP header at its beginning, containing vital information for reliable delivery.
- TCP Header Structure (Key Fields):
- Source Port (16 bits): Identifies the application sending the data.
- Destination Port (16 bits): Identifies the application receiving the data.
- Sequence Number (32 bits): Crucial for ordering. It's the byte number of the first byte of data in the current segment. This allows the receiver to reassemble data in the correct order.
- Acknowledgment Number (32 bits): If the ACK flag is set, this field contains the next expected sequence number from the sender. This acknowledges successful receipt of previous data.
- Data Offset (4 bits): Specifies the length of the TCP header in 32-bit words (indicating where the actual data begins).
- Reserved (6 bits): Future use, always set to zero.
- TCP Flags (9 bits): These single-bit flags are incredibly important for controlling the TCP connection and indicating the segment's purpose.
2. TCP Flags: Controlling the Conversation
These flags act as signals within the TCP header, dictating the behavior and state of the connection:
- URG (Urgent Pointer): Indicates that the Urgent Pointer field is significant. Used for out-of-band data (rarely used in modern TCP).
- ACK (Acknowledgment): Indicates that the Acknowledgment Number field is valid. This is present in almost all segments once a connection is established.
- PSH (Push): Asks the sending application to "push" buffered data immediately to the receiving application.
- RST (Reset): Resets a connection, typically due to an error, a host crash, or to reject an invalid segment.
- SYN (Synchronize): Used to initiate a connection. The first step of the three-way handshake.
- FIN (Finish): Used to gracefully terminate a connection.
- ECE (ECN-Echo): Indicates Explicit Congestion Notification (ECN) capability.
- CWR (Congestion Window Reduced): Indicates that the sender has reduced its congestion window (part of ECN).
- NS (Nonce Sum): Used for protection against accidental errors.
3. TCP Sockets
A TCP socket is an endpoint of a two-way communication link on a network. It's defined by the combination of an IP address and a port number (e.g., 192.168.1.100:8080). When you establish a TCP connection, two sockets (one on each end) are involved in the communication. Applications use sockets to send and receive data over the network.
4. TCP Connection Establishment: The Three-Way Handshake
Before any data is exchanged, TCP establishes a reliable connection using a three-way handshake:
- SYN (Synchronize): The client sends a SYN segment to the server, indicating its intention to establish a connection and suggesting an initial sequence number (ISN).
- SYN-ACK (Synchronize-Acknowledgment): The server receives the SYN, sends back a SYN-ACK segment, acknowledging the client's SYN (ACKing the client's ISN + 1) and providing its own ISN.
- ACK (Acknowledgment): The client receives the SYN-ACK, sends back an ACK segment, acknowledging the server's SYN (ACKing the server's ISN + 1).
At this point, a full-duplex, reliable connection is established, and data transfer can begin.
5. TCP Data Transfer and Acknowledgment: How TCP Detects Lost Packets
During data transfer, TCP uses sequence numbers and acknowledgment numbers to ensure reliability.
- Sequence Numbers: Each byte of data sent by TCP has a sequence number. Segments carry the sequence number of their first byte of data.
- Acknowledgment Numbers: The receiver sends back acknowledgment (ACK) segments to the sender, indicating the next sequence number it expects to receive. An ACK for sequence number
Xmeans that all bytes up toX-1have been successfully received.
How TCP Detects Lost Packets:
- Duplicate ACKs: If the sender receives multiple ACKs for the same sequence number, it indicates that a subsequent segment might have been lost.
- Retransmission Timeout (RTO): TCP sets a timer for each segment it sends. If an ACK for that segment is not received before the timer expires, TCP assumes the segment is lost and retransmits it. The RTO is dynamically adjusted based on network conditions (Round Trip Time - RTT).
6. TCP Flow Control: Managing the Data Rate
TCP Flow Control prevents a fast sender from overwhelming a slower receiver. It uses a sliding window mechanism:
- Receive Window (RWND): The receiver advertises its available buffer space (the Receive Window) in the TCP header. This tells the sender how much data it can send without waiting for an acknowledgment.
- Send Window (SWND): The sender maintains its own Send Window, which represents the amount of data it is allowed to send before receiving an acknowledgment. The Send Window is limited by the minimum of its congestion window and the receiver's advertised Receive Window.
The TCP Sliding Window allows multiple segments to be "in flight" (sent but not yet acknowledged) simultaneously, improving efficiency. As ACKs arrive, the window "slides" forward, allowing more data to be sent. If the receiver's buffer fills up, it will advertise a smaller (or even zero) Receive Window, pausing the sender until buffer space becomes available.
7. TCP Congestion Control: Preventing Network Meltdown
While flow control manages receiver capacity, TCP Congestion Control aims to prevent network overload (congestion). It dynamically adjusts the transmission rate based on perceived network conditions. This is a critical feature that makes the internet work without constantly grinding to a halt.
Key mechanisms include:
- Slow Start: When a TCP connection begins, it starts by sending data at a very conservative rate (small congestion window - CWND). The CWND increases exponentially for each acknowledged segment, doubling with each Round Trip Time (RTT), until it reaches a certain threshold (ssthresh). This "slowly" probes the network's capacity.
- Congestion Avoidance: Once the CWND reaches the
ssthresh, the growth becomes linear (incrementing by one segment per RTT). This aims to avoid triggering congestion. - Fast Retransmit: If a sender receives three duplicate ACKs for the same segment, it assumes that segment is lost and immediately retransmits it without waiting for the retransmission timer to expire. This helps recover from losses quickly.
- Fast Recovery: Often paired with Fast Retransmit. After Fast Retransmit, TCP doesn't go back to Slow Start's initial small window. Instead, it reduces its congestion window by half and then continues with linear growth (congestion avoidance) from that point. This speeds up recovery after a minor loss.
- Selective Acknowledgement (SACK): Traditionally, TCP uses cumulative acknowledgments (ACKing the next expected byte). SACK allows the receiver to explicitly tell the sender which out-of-order segments it has received. This is a significant improvement, as the sender can then retransmit only the truly missing segments, rather than retransmitting everything after the first missing segment, greatly improving efficiency, especially on networks with high packet loss.
8. TCP Blocks
While "TCP blocks" isn't a standard, well-defined term like "segments" or "packets," it might refer to:
- Blocked Sockets: A TCP socket can become "blocked" if an application tries to send data but the TCP send buffer is full, or if it tries to receive data but no data is available in the receive buffer.
- Data Blocks: More generally, data is often processed in memory blocks before being segmented by TCP.
- Congestion Blocks: During periods of high congestion, TCP's congestion control mechanisms can temporarily "block" or significantly slow down data transmission to prevent overwhelming the network.
Port Numbers
TCP and UDP use port numbers to identify specific applications or services running on a host. This allows multiple applications to share the same IP address and receive the correct data.
Network Address Translation (NAT)
NAT is a technique used to map multiple private IP addresses within a local network to a single public IP address when connecting to the internet. This helps conserve public IPv4 addresses and provides a layer of security by hiding internal network topology.
The Importance of TCP/IP in Today's World
TCP/IP is not just a theoretical model; it's the bedrock of modern digital life. It underpins:
- The Internet: Every website you visit, every email you send, every video call you make relies on TCP/IP.
- Local Area Networks (LANs): Your home or office network uses TCP/IP to allow devices to communicate.
- Cloud Computing: The massive data centers powering cloud services are built on TCP/IP infrastructure.
- IoT (Internet of Things): From smart homes to industrial sensors, IoT devices communicate using TCP/IP.
- Cybersecurity: Understanding TCP/IP is crucial for identifying and mitigating network vulnerabilities and attacks.
Conclusion: A Continuously Evolving Foundation
From its humble beginnings as an experimental protocol, TCP/IP has evolved into the robust and flexible architecture that powers our interconnected world. Its layered design, combined with its sophisticated mechanisms for reliability, routing, flow control, and congestion avoidance, has made it incredibly adaptable to ever-changing network demands. The subtle yet powerful interactions between TCP's flags, sequence numbers, windows, and congestion algorithms are what allow the internet to function so smoothly.
As technology continues to advance, so too will the TCP/IP suite, with ongoing developments in areas like IPv6 adoption, network programmability, and enhanced security features. For anyone working with or interested in technology, a solid understanding of TCP/IP is not just beneficial; it's essential. It's the language that connects us all, and truly comprehending its depth opens up a world of possibilities in networking, cybersecurity, and beyond.